Cyber Security Pro Licence Keys
ESET Cyber Security Pro - ESET Cyber Security Pro, sitename Menu. This is the Header Notice module, use it for promotional or other important messages. Cyber Security With Peter Psl. VMware Workstation 15 Pro Key: FF31K-AHZD1-H8ETZ-8WWEZ-WUUVA.

[KB3255] Enter my Username, Password, or License Key to activate ESET Cyber Security/ESET Cyber Security Pro
Issue
- 'Product not activated' - Checking protection status colors (red/green)
- You receive the notification 'Update information is not consistent'
- You receive the notification 'Invalid username and password'
- Virus signature database updates fail
- Product activation fails
Details
Dell-latitude 7350-detachable-refurbished-touch-screen-laptop, Intel Core M,256 M2 SSD,8 GB DDR3 Ram,13.3 Touch Screen FHD Display, Intel HD Graphic. ESET Cyber Security Pro Crack With Serial key Free. ESET Cyber Security Pro Mac is a new approach to computer security that is truly integrated. The latest version of the scanning engine, combined with email client protection, personal firewall and parental control, uses speed and accuracy to maintain the security of your computer.
ESET Cyber Security and ESET Cyber Security Pro are updated at least once a day with new virus definitions and occasional program component upgrades. These updates will fail if your Username or Password is invalid or entered incorrectly.
Solution
Windows Users|Android users
Version 6 (License Key)
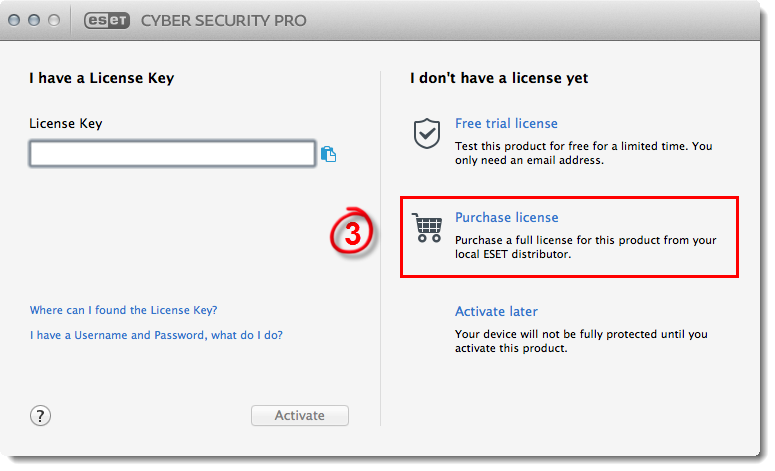
After installing ESET Cyber Security and ESET Cyber Security Pro, you will automatically be prompted to enter your License Key to activate your product. If you skipped this step, or your product is still not activated, follow the steps below:
- Open ESET Cyber Security and ESET Cyber Security Pro. If your product is not activated, it will say Product is not activated in red:
- Click Help → Manage License.

- Type, or copy/paste, your ESET-issued License Key into the License Key field and then click Activate. Click here if you lost your License Key.
- Click Done.
Version 5.x and earlier (Username and Password)
- Locate your ESET-issued Username and Password, which you should have received by email after purchase or first activation of your product. If you cannot locate your Username and Password, visit the Lost License page to have them resent.
- Open ESET Cyber Security or ESET Cyber Security Pro. How do I open my ESET product?
- Press COMMAND + U to open the Username and Password setup window.
Figure 2-1
Click the image to view larger in new window
- Enter your ESET-issued Username and Password into the appropriate fields and then click OK.
Usernames and Passwords
Remember to enter your Username and Password exactly as they are written:
- The username and password are case sensitive
- The hyphen in the username is necessary
- The password is ten characters long and all lowercase
- If you are copying and pasting, make sure you don't select an extra blank space
- We do not use the letter L in passwords (use the number one (1) instead)
- A big '0' is the number zero (0); a little 'o' is the lowercase letter o
Figure 2-2
Click the image to view larger in new window - Click Update → Update virus signature database (make sure you are connected to the Internet). If the update fails, repeat steps 2-5.
Figure 2-3
Click the image to view larger in new window
Russian spies from APT29 responded to Western agencies outing their tactics by adopting a red-teaming tool to blend into targets' networks as a legitimate pentesting exercise.
Now, the UK's National Cyber Security Centre (NCSC) and the US warn, the SVR is busy exploiting a dozen critical-rated vulns (including RCEs) in equipment ranging from Cisco routers through to VMware virtualization kit – and the well-known Pulse Secure VPN flaw, among others.
'In one example identified by the NCSC, the actor had searched for authentication credentials in mailboxes, including passwords and PKI keys,' warned the GCHQ offshoot today.
Roughly equivalent to MI6 mixed with GCHQ, the SVR is Russia's foreign intelligence service and is known to infosec pros as APT29. A couple of weeks ago, Britain and the US joined forces to out the SVR's Tactics, Techniques and Procedures (TTPs), giving the world's infosec defenders a chance to look out for the state-backed hackers' fingerprints on their networked infrastructure.
'SVR cyber operators appear to have reacted to this report by changing their TTPs in an attempt to avoid further detection and remediation efforts by network defenders,' said the poker-faced NCSC today, in an advisory detailing precisely what those changed TTPs are.
They include:
- A severe hole in Pulse Secure's Zero Trust Remote Access VPN software;
- An arbitrary code execution vuln in F5 BIG-IP app delivery controllers;
- An exploitable flaw in the Cisco RV320 WAN router (live code for the exploit exists in the wild);
- A critical vuln in Citrix (Netscaler) ADC load-balancers (publicly disclosed, ironically, by now-US-sanctioned Positive Technologies);
- A critical RCE vuln in VMware's HTML5 client for its vSphere hybrid cloud suite; and
- An exploitable hole in Oracle's WebLogic Server permitting remote code execution
On top of all that the SVR is also posing as legitimate red-team pentesters: looking for easy camouflage, the spies hopped onto GitHub and downloaded the free open-source Sliver red-teaming platform, in what the NCSC described as 'an attempt to maintain their accesses.'
There are more vulns being abused by the Russians and the full NCSC advisory on what these are can be read on the NCSC website. The advisory includes YARA and Snort rules.
The self-preservation society
Separately, the NCSC issued a blog post this morning warning public sector operators of smart city infrastructure to be wary of unnamed hostile foreign countries using these installations to steal data and more.
Comparing the risks to The Italian Job, NCSC chief techie Ian Levy wrote: 'As part of an elaborate heist, a dodgy computer professor (played by Benny Hill) switches magnetic storage tapes for the Turin traffic control to create a gridlock.'
Drawing on this, the NCSC has published a set of 'connected places cyber security principles' for operators of public spaces with connectivity kit and sensors in them.
Cyber Security Pro Licence Keys Free
Why the sudden focus on smart streetlights and all the rest of it? Though the NCSC wouldn't be drawn, a clue lies in El Reg's inbox. For the past few years Huawei has been one of the most aggressively marketed smart city vendors. The Chinese company's website boasts of its 'smart city solution service', which consists of covering your dumb pavements and stupid trees in sensors that may or may not be remotely accessible by Beijing.
More prosaically, the risk in smart cities is the direct control of operational technology; industrial equipment such as CCTV, streetlights and access control systems. We understand at least one UK council is removing some smart city gear after having had a think about the wisdom of installing it. ®